Problem
You need to search and replace large registry databases with a set of new values. You have a third-party utility to do the job, but this utility can only update values writable by administrator. Thousands of registry keys are owned by NT Service\TrustedInstaller and protected even for Administrators. What to do?
If you simply use REGEDIT to take ownership and add full rights to Administrator to all registry at once, you will definitely achieve the goal, but you will ruin the intricate security permissions for dozens of system service accounts that populate registry security. Windows will run but many features like Windows Update will become broken.
Solution
The plan of action includes 5 steps in this order:
-01- Save registry security of a branch that you about to update into a file
-02- Set Administrators as an owner of all the keys and sub-keys
-03- Grant Administrators full control of all the keys and sub-keys
-04- Perform your updates and replacements with your favorite registry tool
-05- Restore registry security to its original state using file created in step 01.
Here are the details.
-00- Download a small utility SubInACL from Microsoft:
http://www.microsoft.com/downloads/en/details.aspx?FamilyID=e8ba3e56-d8fe-4a91-93cf-ed6985e3927b
Installation places 3-4 files in a directory of your choice. Place file subInACL.exe in a directory close to root, where you are planning to do all the magic. This utility is dated 2004, but it understands security settings of current operating systems including Windows 7. Moreover, all examples here are done over Windows 7 security. And yes, this utility works with 64-bit registry.
-01- Save Registry Security
subInACL /noverbose /output=C:\T\Software.txt /subkeyreg HKEY_LOCAL_MACHINE\Software /display=sddl
This command will generate a 75 MB file. This is all the information you need to restore your Registry security for SOFTWARE registry branch. You can use similar command to save registry security of other registry branches including loaded hives. This command takes from 14 to 22 seconds to run.
Please note last option /display=sddl. This option allows to save security user name in S-1-x-x format. This is important for 2 reasons. First, is saves time, because there is no need to convert each user from SDDL format to a User Name. But the main reason is that this command will work even if users are not defined on current Windows instance (when registry branch is imported from other machines or instances). There is this tricky little user NT Service\TrustedInstaller that makes the use of this switch a must.
-02- Set New Owner
C:\T\subInACL /subkeyreg HKEY_LOCAL_MACHINE\Software /setowner=Administrators
This command will set Administrators as an owner of all registry keys and sub-keys in a selection. This command takes 31 seconds to run.
-03- Grant Full Control
C:\T\subInACL /subkeyreg HKEY_LOCAL_MACHINE\Software /grant=Administrators=F
This command sets Administrators with full access rights to all keys and sub-keys in a given registry branch. This command takes 48 seconds to complete.
-04- Update, Edit and Replace
Now the entire registry branch is open for Administrators to edit, update, bulk replace and merge.
Using your favorite third-party registry tool or simply using Export, Replace and Merge back, perform your required manipulations. I like this little-known search and replace utility from – http://www.funduc.com/rtshareware.
-05- Restore Registry Security
This is the most important step here. This should be the focus of your testing. All other steps can be done using other tools and methods. This step is the point of this article.
C:\T\subInACL /playfile C:\T\Software.txt
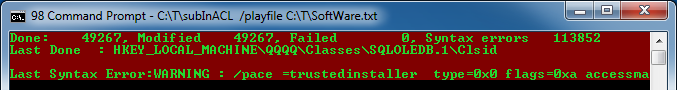
This command restores back registry security of your branch using file that you created in a first step. This step takes 43 seconds to complete all 142711 registry branches . Note that you simply instructing subInACL to run a security script stored in C:\T\Software.txt
Once again, your point of testing here should be some branch (for example HKEY_LOCAL_MACHINE\SOFTWARE\Classes\xmlfile\CLSID) owned before by TrustedInstaller. After completing this test this branch once again should be owned by TrustedInstaller.
Unexpected Registry Security Recovery Use – “Restore to Factory”
One more exciting and unexpected application of this approach is resetting registry security to original factory settings. Imagine your Windows 7 registry security is really messed up. You need to restore, but you do not want to restore to previous point in time. You want to keep all the software and setting as it is, but only reset the registry security.
You can run a new parallel Windows 7 install, save Registry security for SOFTWARE and SYSTEM in there. Then, come back to your precious messed up instance and restore “factory” registry security and keep all the registry values in place. I just tested it. It works.
Of source, only security of original registry branches will be reset. And there is no 100% one-to-one match in long seemingly random CLSID branches. But 80% of the registry keys were matched, and security on those were reset to “factory”! I would definitely try this method tomorrow to recover an instance that just refuses to boot.



This is a reply to Rokas Gustys. Thank you for visiting!
QUESTION: Could you please explain how to access 64-bit registry keys? It redirect me to the Wow6432Node.
ANSWER: Please clarify. I do not understand the question: “It redirect me to the Wow6432Node”? What it? REGEDIT?
Could you explain how this works to access 64-bit registry keys? Cause for me all it does is redirect me to the Wow6432Node (32-bit keys)
thanks for trying, I found my answer elsewhere :) much thanks!
(signed not a robot :) )
I would like to take this dialog offline, and here is why:
— I still can’t comprehend the question;
— 35% of me suspecting a very advanced robot on the other side that sends auto-messages, and sprinkles grammatical errors and misspell just to be convincing.
What do you think?
LOL Microneasia?? Where did you get that from?? HAHA
Am from USA.
Sorry for question, was jut wanting to add something to the subinacl reset.cmd batch file that will “save” the errors,events it does to a certain directory and text name.
Trying to figure out how to do it, and where i file to put it.
I did not understand the question, but I am impressed with your email address. Are you actually from Federated States of Micronesia?
We recommend that you never save anything into your root. Create a T or TEMP directory instead. You can place all your output there, and reference this file, when restoring your registry security back.
Good luck and thank for your comment.
thank you thank you for this page, it sure helped.
I have my subinacl in the C root directory, am going to run it, would like to put the rference in my reset.cmd batch file (for the subinacl) to save a textfile to C:/(root) to I can review when its done running.
Can you help please?
The reset.cmd I want to adjust to save my subinacl report to is here
[code]
http://blogs.msdn.com/b/astebner/archive/2006/09/04/739820.aspx
[/code]
where and what would I put in to save the report to C: when done?
Great information! I’ve been looking for something like this for a while now. Thanks!